With a shift to remote working, social media channels have become ever more popular with businesses increasing their visibility. A typical enterprise has multiple corporate social media accounts –Twitter, Facebook, Instagram, YouTube, LinkedIn and other outlets. This brings an added risk to the business if your IT security team doesn’t have an oversight of privileged users and accounts and poses a number of challenges, for example:
- How do you securely share the credentials for these accounts?
- How do you control who has knowledge of the credentials?
- How do you make sure these credentials are stored securely? For instance, how do you ensure no-one has written the credentials on a post-it note?
- How do you know who is using the accounts and when? For example, the posting of unauthorized confidential information – how do you know who did it?
- How do you make sure passwords are changed periodically without affecting the business?
- How do you know if the user has moved-on, maybe works for a competitor and still have access to social media accounts?
The solution – Thycotic Secret Server is an enterprise-grade Privileged Access Management (PAM) solution that protects your privileges for service, application, root and administrator accounts. Allowing you to address all, and more, of the above issues enabling security and IT teams to gain even tighter control and visibility of privileged access and improve productivity.
Let’s work with a simple scenario.
Lynda holds a role within the marketing team with the task of promoting a webinar via social media. In order to access the company account Lynda accesses Thycotic secret server via her corporate account which gives her access to Secret Server. As she is a member of the marketing team, she has access to Secret Server Item containing the LinkedIn account credentials (these items are called secrets in Secret Server).
A number of controls can be put in place:
1. In order to access the password Lynda requests access to the credentials and the request is approved by a more senior person in the organization. This provides the following information:
a. The time Lynda requested access to the credentials.
b. Who approved and the request time of approval.
c. Once the approval has been granted only Lynda has these credentials at the time (checkout).
2. Once Lynda has access to the credentials she discovers (see screenshot) she cannot “see” the password associated with the account, instead she can see a link that she can click to access the LinkedIn account; this means that this password can be:
a. Complex with many characters and there is no requirement to remember it.
b. It can be changed without affecting anybody.
c. If Lynda leaves the organization she will not know the LinkedIn password.
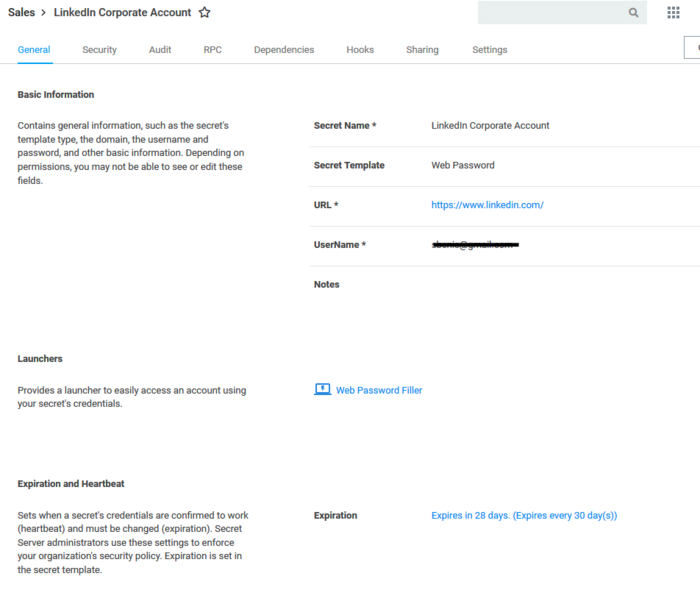
3. By clicking the link, a new browser is opened and redirects Lynda to the LinkedIn login page, Secret Server fills in the username and password and logs Lynda into LinkedIn. In addition, Secret Server can now record Lynda’s session and create a video of Lynda’s LinkedIn session.
Security administrators can either view while the session is in progress or later once the session has finished, this means:
a. If something needs to be investigated at any time all the information is available, the security officer is able to confirm who did what, when, who approved it and so forth.
4. Once Lynda finishes publishing the Webinar information she returns to Secret Server and checks-in the credentials to Secret Server enabling another user to access it, if required.
In summary, automation, web session recording and session launching capabilities tighten administrative control so you can focus on what’s really important and lower your risk. Recent enhancements to Secret Server provide organizations with a powerful solution to take control over their privileged account attack surface. As always, maintaining user privacy is a key concern. Web session recording captures only activities related to privileged sessions and not personal applications open in a web browser.
With more frequent attacks of this nature, it’s time for organizations to take a closer look at how they manage their social media accounts. Privileged Access Management can play a critical role in protecting access to social media platforms, preventing embarrassing incidents and stopping cyber-attacks before irreversible damage can be done to your business.
Start your free 30-day Secret Server trial now.
Be the first to hear about news, product updates, and innovation from proofid










