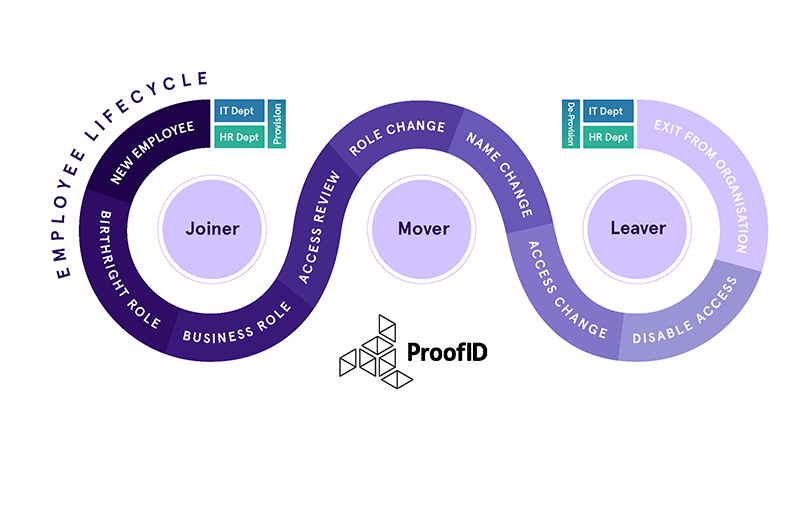
Rather than employees commuting full time, most companies have fully embraced hybrid approach of in-person and work from anywhere models. But for all its benefits, digitisation has also introduced more security risks and user access to manage — both human and not. In fact, as many as 80% of organizations say the shift to remote work has increased their focus on identity security.
According to a recent Forrester Report, How to Secure and Govern Non-Human Entities, the amount of remote and non-employee workers sharply increased in recent years, and it doesn’t show signs of slowing down. That means more types of users, non-human entities, devices, and data sources than ever to protect and manage. This compounded with the steady migration of workloads to diverse cloud hybrid infrastructures makes for an increasingly complex dynamic.
Identity security is no longer a “nice to have” — it’s essential. Most modern businesses know this and have implemented identity management including some combination of access management, user provisioning and identity governance. Now, the idea of moving identity security fully to the cloud has many of these same businesses considering their options. They may be evaluating the possibility of upgrading an existing identity management solution from on-premises to a cloud-based version while others prefer to refresh with a new SaaS identity security solution. Whichever is the chosen path, moving identity security to the cloud, enables connections to critical applications virtually, seamlessly, and securely.
Benefits of Identity Security in the Cloud
Rapid deployment with zero maintenance burden
A much faster and lower risk implementation due to the in-product capabilities available ‘out of the box’. Cloud solutions can do the heavy lifting of managing and securing for you.
Built-in identity security best practices
Industry-leading technology uses years of experience across thousands of identity programs to deliver only the best in identity and access management.
Automatic updates for minimized IT workloads
Identity security in the cloud delivers features and maintenance updates across all core components, requiring zero downtime and reducing in-house IT effort.
Immediate ROI, faster service, and tighter security
Cloud-based identity governance can accelerate the time to value on access certifications from one year to one month, automate new user access from 14 hours to 2.5 minutes, and deprovision worker accounts from 30+ days to just minutes. Role modelling efforts that used to take days to implement common access and birth right roles can be quickly and easily discoverable.
Improved security, and reduced risk overall
AI capabilities minimize certification fatigue and introduce data-based decision-making for Zero Trust, zero deficiencies, and zero worries.
Make Moving Identity Security to the Cloud Simpler
At ProofID, we understand that moving IAM to the cloud can be tricky. The process can seem daunting and complicated. Our certified IAM experts work with you through every step of the transition process or, if you’re starting from scratch in the cloud, we’ll help you prepare for a seamless deployment that aligns core business processes, roles, and applications right into your cloud-based identity security platform.
With most identity security platforms, five applications usually take 12 weeks to reach basic provisioning, access review, and access insights — ProofID can enable you to configure two applications in just eight weeks.
How does it work?
Initially, we will complete an assessment of your identity environment. We then start moving to stand up the core system. From there, over two weeks, our team will enable an authoritative source, granting visibility into the base set of users and privileges. The final two weeks we focus on enabling you and your team to be in control, allowing you to view, manage and regulate all identities.
What Can ProofID Help Me Do?
Let’s start with strategy. All ProofID relationships begin with planning and preparation. We’ll help you identify both short and long-term goals, as well as create an application and functionality project rollout plan. This will help set expectations, and identify which applications, roles, and policies need prioritising.
Preparing you for rollout, the first step is to assess what users, permissions, and access controls already exist in third-party IAM platforms, whether it’s in a legacy or homegrown IAM solution we need to discover where all the core identity components are before we bring them together. From there, we move to deployment. Depending on your goals and priorities, we will customize a plan that works for you in the immediate and longer term.
Your Cloud Identity Security Partner
When you choose ProofID to assist with your implementation of an identity security platform, you’re not just choosing an identity security provider, but a partner in delivery. We strive to enable self-sufficiency in managing your solution after implementation and take a hands-on approach in training so your team can take an active role in future delivery. Even after implementation is complete, ProofID IAM experts and executives are available to answer any question you may have about secure access management, around the clock.
Organizations can also unlock the benefits of our AI services. Automation affords not only ease of use, but peace of mind by removing the possibility of human error from the equation. Our services allow you to maximize the use of AI Services to automate the management of all user access, allowing you to spot risks as they arise, identify common trends to consolidate roles or automate tasks, and provide actionable insights for course correction as needed.
We know the implementation process can be an intimidating one, so we’re here for you every step of the way. Contact us.
Be the first to hear about news, product updates, and innovation from proofid