Ensuring your IT systems are secure as possible can be a painstaking task, here at ProofID we tend to use Qualys to automate our IT security auditing, compliance and protection.
In this blog we’re going to look at how to enable SSO to Qualys using PingFederate as the Identity provider.
First you must raise a support ticket with Qualys at www.qualys.com/support to request enabling SAML2.0 SSO support to be enabled on your account; this request must be made by (or authorised) by the primary contact within your Qualys tenant. Within the support ticket you must provide:
- Your SAML2.0 Entity ID
- Your signing certificate, base64 encoded
- The URL for HTTP Redirect URL for SP Initiated requests, e.g. https://identity.example.com/idp/SSO.saml2 within PingFederate
- Your QualysGuard subscription ID
Once you have raised the ticket with Qualys they will process the request and let you know when its complete providing details of their SAML endpoints and crucially an idm_key which is needed for IdP initiated requests.
Now we have these details the next step is creating the SAML connection within PingFederate, this is a fairly standard SAML 2 connection though Qualys does not provide SAML2.0 metadata so the connection needs to be setup manually.
When creating the connection, the following steps should be followed:
- Set the Partners Entity ID to: QualysGuard_SharedPlatform-SAML20-SP
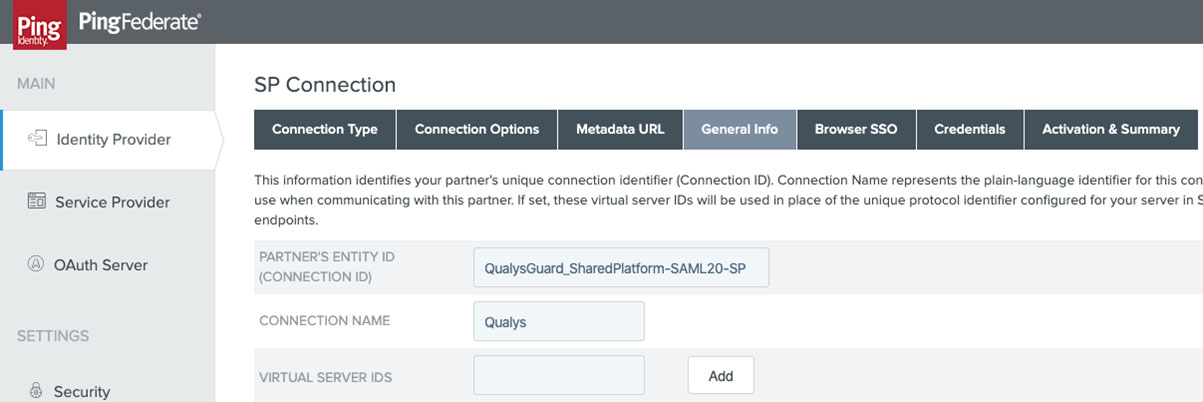
- Qualys supports both IdP and SP initiated SSO so both options should be selected
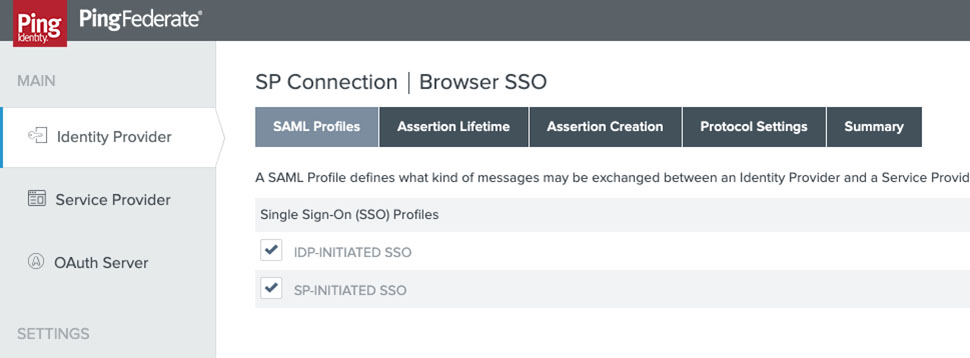
- The transient identity mapping is used with the unique identifier for the user being passed in an attribute named qualysguard_external_id.
- To configure this on Identity Mapping select Transient and choose to include attributes in addition to the transient identifier:
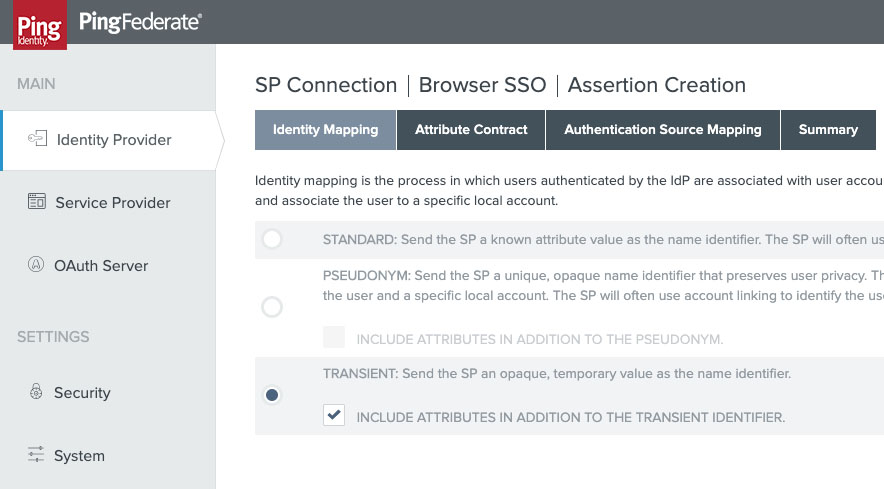
- On the attribute contact extend this with an attribute named qualysguard_external_id with the format of “urn:oasis:names:tc:SAML:2.0:attrname-format:basic”
- Bind your chosen authentication adapters or policies and then fulfil the qualysguard_external_id within the attribute contract, here we’re using the value from the employeeNumber field in Active Directory:
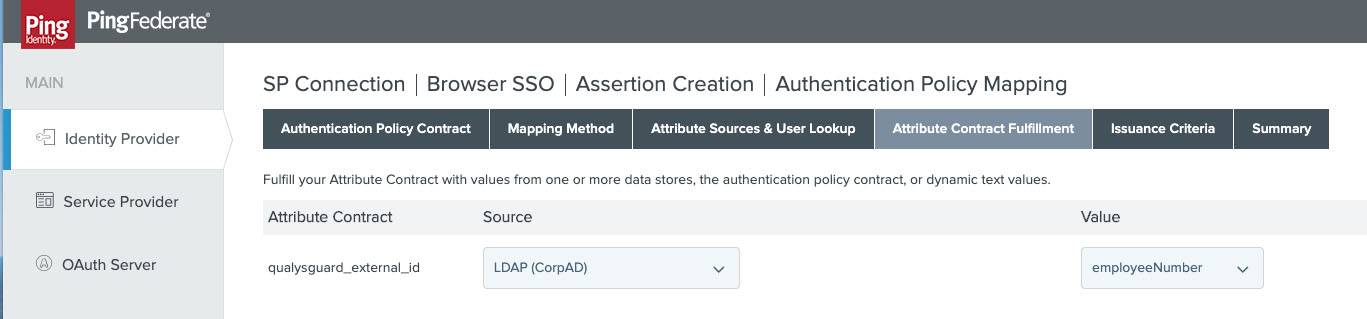
- Issuance criteria can be configured to further restrict access to Qualys
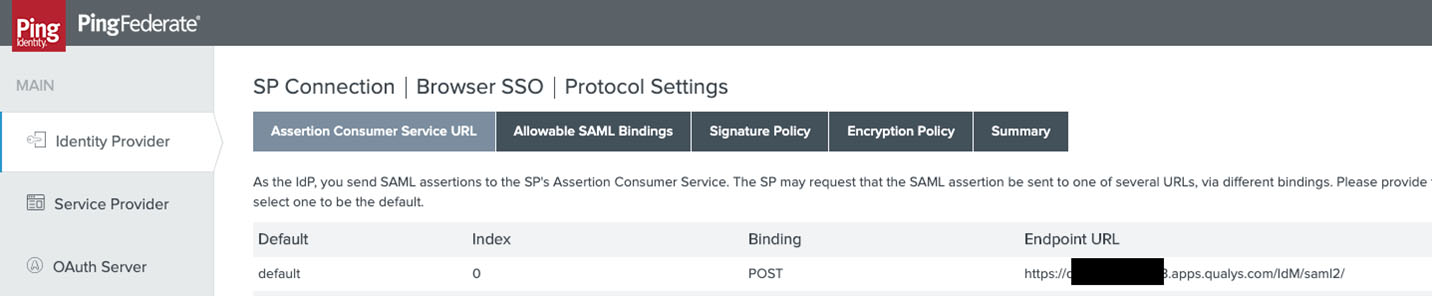
- Qualys supports the POST and redirect bindings for SAML2.0, and the endpoint should be specified as supplier by Qualys:
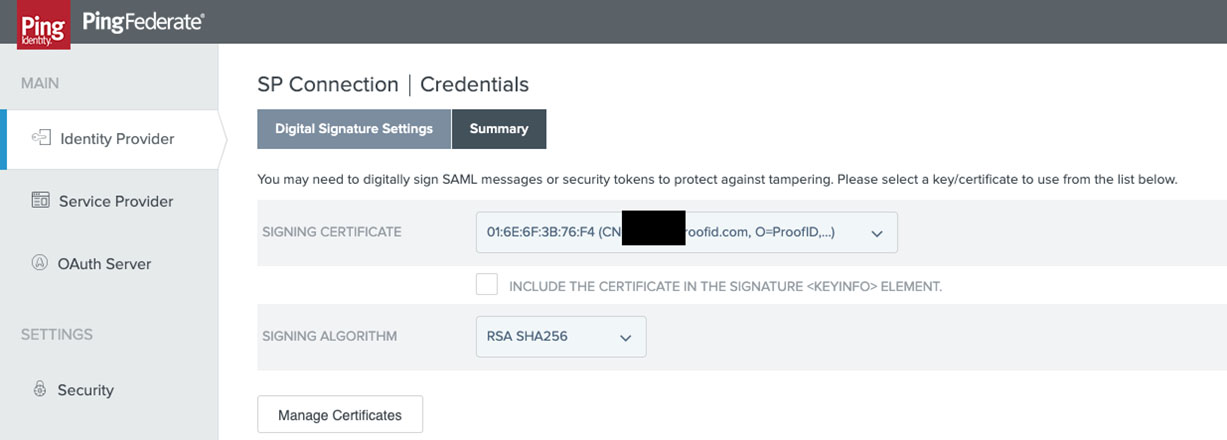
- The defaults for signatures are acceptable for Qualys with the signing algorithm being set at RSA SHA256.
The next step is to set the external ID on your user accounts within Qualys. This ID must match a unique identifier that you pass within the qualysguard_external_id attribute in your SAML assertion, ideally this valid should be immutable as such the use of email address is not a good choice. Here at ProofID we generate a unique value on account creation that we utilise, that way when a user’s name changes we don’t need to update the linking key across the systems.
To set the unique ID we go into the user management section of Qualys and choose to edit the users Basic Details and set their External ID:
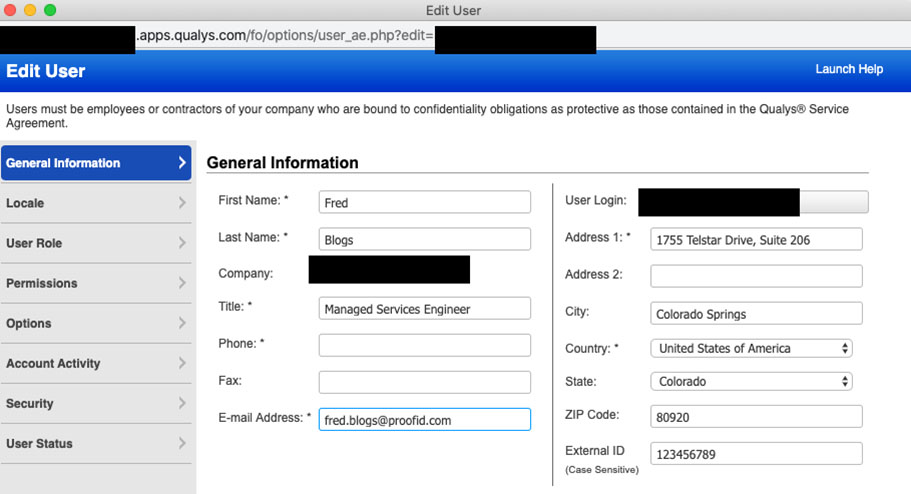
NOTE: only the primary account owner is able to initially edit external ID’s. Once you have logged in via SAML and have suitable rights other users can edit the external ID.
You then need to enable on a per user basis the use of SAML for login, again on the Edit Basic Users Screen select “Security” and choose to enable SAML SSO:
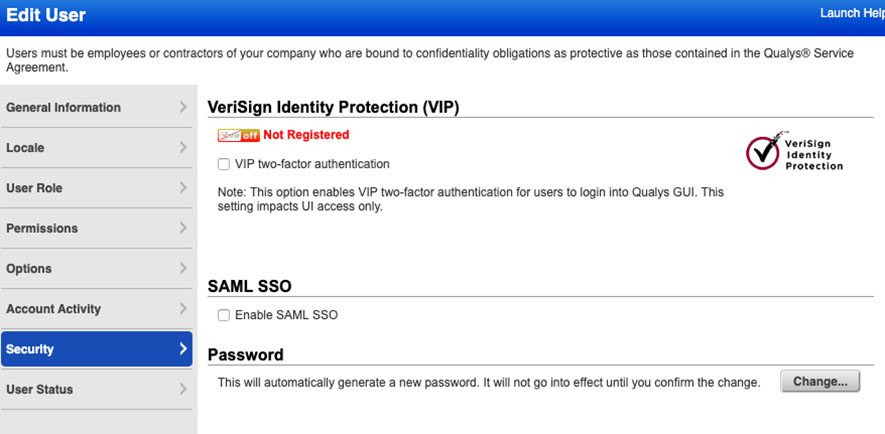
Once you click save the user will no longer be able to login using their existing password and will receive an email with a link to be able to login, this is an SP initiated URL and will be in the format:
https://TENANT.apps.qualys.com/fo/login.php?idm_key=saml2_KEYID
Notice here we have an idm_key appended to the URL, if we wish to use IdP initiated SSO then this idm_key is passed as the RelayState in the SAML request which in PingFederate is set on the IDP initiated URL as the TargetResource parameter. This means that the IdP initiated URL for Qualys would become:
https://identity.example.com/idp/startSSO.ping?PartnerSpId=QualysGuard_SharedPlatform-SAML20-SP&TargetResource=%3cIDP_KEY_VALUE>
Take advantage of ProofID’s in-house Ping Identity technical knowledge and expertise and contact us.
Be the first to hear about news, product updates, and innovation from proofid










