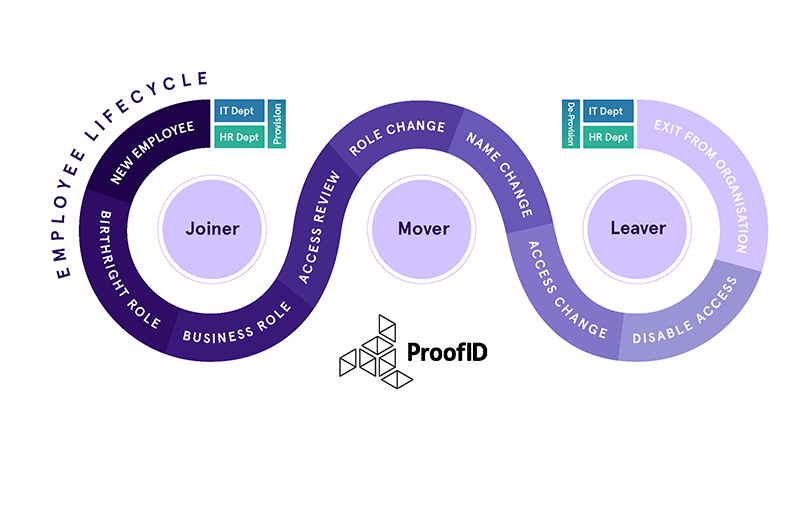
Today identity security extends far beyond your internal workforce. Most organizations now rely on an extended network of contractors, suppliers, and B2B partners — all of whom need digital access to critical systems and data. Yet many identity governance programs still focus solely on full-time employees.
That’s where Non-Employee Risk Management (NERM) comes in.
Today identity security extends far beyond your internal workforce. Most organizations now rely on an extended network of contractors, suppliers, and B2B partners — all of whom need digital access to critical systems and data. Yet many identity governance programs still focus solely on full-time employees.
That’s where Non-Employee Risk Management (NERM) comes in.
What Is NERM?
Non-Employee Risk Management (NERM) is the process of identifying, governing, and securing digital identities for users who sit outside your organization’s HR system. These include:
- Contractors and consultants
- Partner and supplier personnel
- B2B customers and ecosystem collaborators
- Temporary and seasonal workers
- Volunteers, researchers, or visiting academics
- Agency or clinical staff in healthcare settings
These users are essential — but often managed inconsistently, through spreadsheets, emails, or siloed systems. The result?
- Over-provisioned access that lingers after contracts end
- Unclear ownership of external identities
- Compliance and audit gaps
- Expanded attack surface across your IT environment
NERM introduces the automation, visibility, and control needed to manage these non-employee identities with the same rigour as your employees — strengthening both security and compliance.
Why NERM Matters
As organizations expand their digital ecosystems, the number of third-party and partner identities grows rapidly. Cloud adoption, supplier collaboration, and outsourced service models make manual management impossible to scale.
Without NERM, enterprises face:
- Shadow identities – unmanaged or orphaned accounts that stay active after projects finish
- Manual onboarding bottlenecks – slowing productivity
- Audit blind spots – non-employees excluded from compliance checks
- Inconsistent processes – each department managing access differently
Auditors and regulators increasingly demand consistent controls across all identities — not just employees. Whether you’re in banking, higher education, retail, healthcare, or utilities, NERM has become essential for reducing risk and maintaining compliance.
Real-World NERM in Action: Industry Use Cases
Banking and Financial Services
A financial institution depends on hundreds of third-party IT consultants and service partners. By integrating its vendor management system into its identity governance platform, it automated onboarding and access reviews, reducing dormant accounts by 70% and ensuring compliance with internal audit requirements.
Insurance Broker
An insurance brokerage firm relies on independent agents and partner firms to serve regional customers. NERM ensures every external user has time-limited, sponsor-approved access to quoting and claims systems, maintaining FCA and GDPR compliance while reducing manual admin by 60%.
Education
Universities collaborate with visiting academics, research partners, and contractors. With NERM, they can now automate joiner–mover–leaver processes for these non-employee identities, ensuring access aligns with academic schedules and funding timelines — without increasing IT workload.
Retail
A large retailer hires temporary staff during seasonal peaks. NERM automates onboarding for these short-term roles, granting immediate access on day one and automatically removing it when contracts expire — maintaining efficiency without compromising security.
Healthcare
A healthcare provider that works with agency nurses and temporary clinicians now uses NERM to enforce time-bound, policy-based access. This ensures patient records remain protected while supporting staffing flexibility across multiple facilities.
Utilities
A regional energy provider works with outsourced engineering firms and IT contractors. NERM delivers complete visibility and control over who can access critical systems, helping the organization comply with industry-specific cybersecurity regulations and reduce the risk of insider threats.
Telecommunications
Telecoms operators face increased scrutiny under the UK Telecommunications (Security) Act (TSA), which requires operators to mitigate supply-chain and access risks. NERM enables telecoms providers to manage the full lifecycle of vendor, contractor, and partner identities — ensuring compliance with the TSA’s mandate for continuous risk assessment, least-privilege access, and rapid deprovisioning when relationships end.
B2B & Partner Ecosystems
Many organizations now operate within complex partner networks. For example:
- A technology vendor providing access to distributors, managed service partners, and resellers through shared portals.
- A manufacturing company collaborating with supply chain partners that need access to logistics or design platforms.
- A regional healthcare network partnering with third-party labs or telehealth providers for shared patient data access.
In each case, NERM ensures partner and B2B identities are governed consistently — automating provisioning, enforcing least-privilege access, and delivering full audit trails without disrupting collaboration.
The Core Pillars of Effective NERM
- Authoritative Source Integration – Connect vendor, partner, or CRM systems as trusted identity sources.
- Automated Lifecycle Management – Enforce consistent joiner–mover–leaver processes for all external identities.
- Clear Ownership – Assign internal sponsors for each contractor, partner, or third-party account.
- Policy-Based Access Controls – Apply least-privilege principles automatically.
- Continuous Compliance Monitoring – Maintain audit readiness across your extended ecosystem.
How ProofID Helps
At ProofID, we help organizations across financial services, higher education, retail, healthcare, and utilities gain control over non-employee and partner risk through our advisory, implementation, and managed services.
Our experts can help you:
- Assess your current exposure to unmanaged and partner identities
- Design a scalable NERM framework aligned with your security strategy
- Implement automated controls using leading identity platforms
- Provide managed services to ensure continuous governance and reporting
If you’re unsure who’s accessing your systems — or how long they’ve had that access — it’s time to take a closer look at Non-Employee Risk Management. Let’s make every identity in your ecosystem — employee or not — visible, governed, and trusted.
1 “93 % of organizations had two or more identity-related breaches in the past year.” CyberArk+2CyberArk+2
2 “In 2022, 20 % of data breaches were linked to third parties.” IBM
3 “Dormant service accounts with privilege were found in more than 70 % of enterprise environments.” scworld.com
Be the first to hear about news, product updates, and innovation from proofid