The Future of Workforce Identity Security.
back btn
Resources
All categories
All content
Upcoming events
Blog

28 Oct 2025 - 5 min read
Managing the unmanaged: Why organisations need Non-Employee Risk Management (NERM)

24 Oct 2025 - 3 min read
ProofID & BECU: Celebrating our Ping Identity Better Together Excellence Award 2025
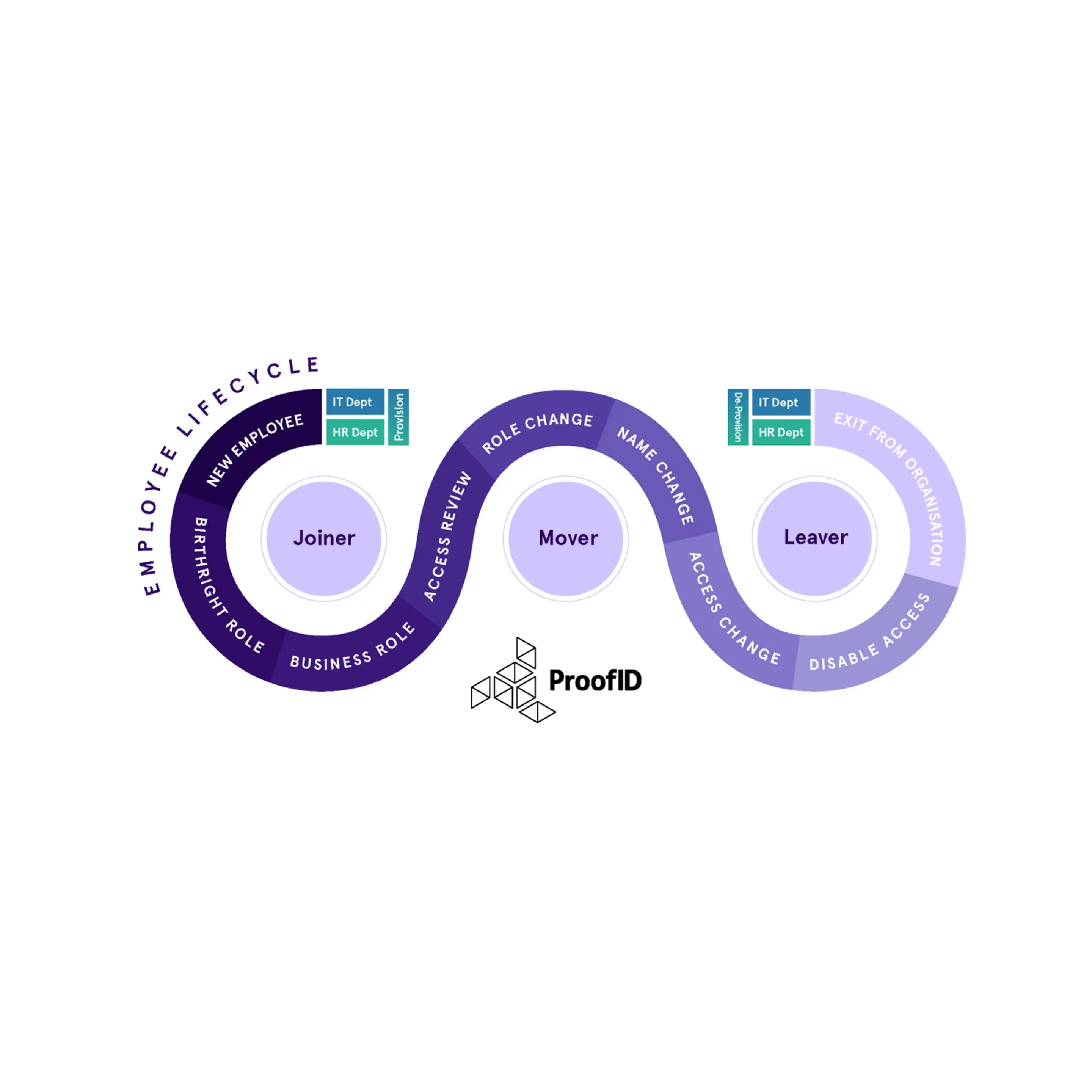
22 Jul 2021 - 4 min read
Role-driven lifecycle management – Automating the joiner, mover, leaver process
.webp)
7 Jul 2020 - 5 min read
5 key questions to ask your Identity Governance and Administration (IGA) vendor
%20is%20a%20cyber%20security%20high%20priority%20(1).webp)
30 Mar 2020 - 1 min read




.webp)






.jpg)



.webp)
.webp)







%20is%20a%20cyber%20security%20high%20priority%20(2).webp)
%20explained%20(1).webp)

.png)
.webp)


.png)

.webp)